The crypto industry is currently in a fickle state. No, I’m not talking price action-wise, I’m talking about it from an infrastructural standpoint.
Let’s summarize the current state of affairs.
Blockchain scalability is no longer a real issue, wallets are now intuitive and easier to use for the average person, and interoperability issues and liquidity fragmentation across networks are gradually disappearing. That’s all great.
But with this as the backbone, the next step for the industry is to have a bunch of crypto-native or crypto-enabled applications that break into the mainstream - whether that’s purely financial applications or other types of consumer applications.
Here’s where the hurdles begin to pop up.
Risk control standards in the onchain world are effectively non-existent. Over $150 billion worth of illicit activity took place onchain in 2024, and this is only from what was tracked; that number in reality is probably a lot higher.
To add to this, the rates of fraud and disputes are 4x and 5x higher than in traditional e-commerce, respectively.
So what does this mean?
For crypto applications to reach mainstream adoption, they also need the same level of safeguards and compliance standards as mainstream applications today.
The current onchain economy is simply not set up for this.
Each application has to build its own safeguards and risk controls, creating siloed controls.
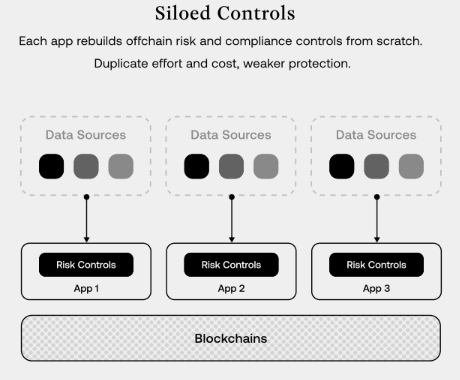
This increases costs, technical load, application complexity, and, in reality, doesn’t do much at all for onchain risk management; the issues still persist. Things right now are simply inefficient.
Yes, there are workarounds where protocols or institutional players use offchain solutions or offer products behind private walls, but then you’re sacrificing the open, composable, and global liquidity of crypto that makes it so special.
The fact of the matter is that, even though this is not a problem that is often discussed, it is actually a major adoption hurdle.
There are potentially trillions of dollars and billions of users exposed to risk of non-compliance, fraud, scams, etc., because applications lack simple, built-in ways to implement risk controls and maintain compliance.
This is precisely where Newton Protocol steps in with its onchain policy engine.
The Magic Labs team (core developer of Newton Protocol) already has experience solving adoption hurdles by bringing millions of new users onchain through its embedded wallet solution. Now it's taking the next step to solve risk at scale to bring in the next major wave of adoption.
What is Newton Protocol?
Newton Protocol is a decentralized policy engine that allows compliance, risk, and business rules to be embedded directly into transaction execution without affecting applications' functionality for the end user.
Newton is looking to spearhead an onchain paradigm shift, moving risk controls away from a siloed model, where individual applications build their own risk controls, toward a shared model in which risk controls are applied across applications through Newton Protocol.
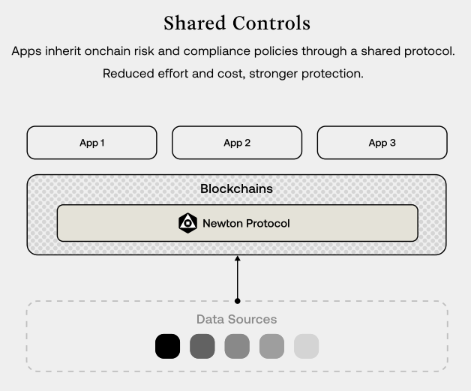
The idea is to take the inefficiencies of existing compliance, an area where upwards of $270 billion is spent in a year by applications, and make it into something ubiquitous and efficient for everyone involved.
Here’s how it works.
Step 1: Write a policy
The first step is for developers to either write new policies or reuse existing ones.
These are the rules for transactions and other actions onchain. It makes policies programmable and enforces business rules (things like spend limits, KYC checks, and so on) at the smart contract layer.
There are two main elements to this.
The first is the code, written in Rego (a declarative policy language), which defines conditions for allowing or denying actions.
It starts with a default ‘deny’ and then changes to allow based on inputs such as transaction details.
For example, a policy may check for daily spending limits and then allow the transaction if it fits the application's policy rule.
The second element is the data oracles that the code can reference. It fetches offchain data for whatever the application's purpose may be - things like price feeds or attestations.
Once written, the developer publishes the policy to Newton Protocol registry, where it is stored and used for execution. The same policies can also be used by other protocols, creating a shared layer.
An example would be a stablecoin issuer creating a policy to “only allow transfers to addresses that are KYC-verified.”
Step 2: Connect smart contract
Once a policy is created and made available in Newton's registry, developers can simply add a lightweight code snippet to any smart contract to connect their application to Newton's policy engine.
That’s it, just a couple of lines of code, and an application has programmable compliance onchain.
With this being implemented in the smart contracts, all transactions made through the protocol have automatic pre-transaction checks backed by cryptographic attestations.
Step 3: Automatic protection and compliance
Once the policy is implemented in the smart contract, the backend technical lift is now complete.
For the user, nothing really changes. They interact with the application as they always would; the only change is that onchain actions that do not comply with the policy will be blocked automatically.
Let’s run through a scenario of how this would work.
A user submits an intent (for example, a transfer). This intent is packaged as a task and sent to Newton Protocol’s Actively Validated Services (AVS) network, which is a decentralized network of nodes/validators.
The AVS network then evaluates the task offchain. They fetch the required data and run it against the policy logic to generate an attestation. This attestation is then aggregated into a consensus proof.
The consensus proof is submitted back onchain to Newton Protocol, which verifies the proof and determines whether the transaction should be allowed or blocked.
Voilà! Just like that, you have automated verifiable compliance.
Step 4: Verify on Newton Explorer
Finally, all the elements of the policy are transparent and verifiable on the Newton Explorer. Whether you’re a user, auditor, developer, or a third party, the Newton Explorer enables you to check all transactions and whether the different rules were complied with.
The explorer makes compliance and risk controls visible to anyone, allowing them to scrutinize and verify the policy determinations, but without the ability to access underlying personal information due to the protocol’s privacy-preserving design.
In addition, it’s a single, unified interface for all crypto compliance, so imagine a third-party auditor verifying whether compliance standards for a specific protocol were met. They can find it on the Newton Explorer in seconds.
It also acts as a great source for modelling and testing. With so much data available, other developers and users can run data against any policy and see how it behaves with evaluating tasks and allowing/blocking transactions.
A scenario of Newton Protocol in action: Stablecoin issuer

Okay, now that you understand the behind-the-scenes workings of Newton Protocol, let’s run through a real-life scenario of the protocol in action.
A major benefactor of Newton Protocol’s policy engine will be institutional participants.
Picture an institutional player like a big bank or financial institution trying to issue a stablecoin for a certain country's native currency.
There is a whole suite of controls and compliance standards that will need to be put in place before they openly distribute the stablecoin on crypto’s global financial rails.
Previously, they would have to configure their own rules in a centralized manner in their application's UI or backend.
Now, with just a couple of lines of code added to their smart contract, they can programmatically enforce rules through Newton Protocol and its policy engine.
The institution can also implement pre-existing policies, or, if not, create its own version very easily.
They can implement controls like:
- KYC checks
- Accreditation verifications
- Jurisdictional restrictions
- Sanction screening
- Spending limits
- Limits based on address risk score
With all of this implemented, the issuer can demonstrate that the stablecoin enforces defined compliance and risk policies at the contract level, while still operating like any other onchain stablecoin.
This gives regulators, partners, and auditors stronger, verifiable evidence about how the asset is designed to be issued, distributed, and used in compliance with applicable regulations and improves the issuer’s ability to deter and detect higher-risk activity.
This same example can expand to RWA protocols, DeFi vaults, and so on.
Newton Protocol is tapping into a market that most of us slinging shitcoins on the daily have not even thought about.
Newton Protocol’s architecture
There are four key design principles behind Newton Protocol:
1. Privacy-preserving - A lot of the policy may involve handling sensitive data (e.g., KYC and AML). Newton Protocol ensures that policies can be enforced without exposing this data, using trusted operator networks and ZK proofs.
2. Credibly neutral - As mentioned earlier, the policies are enforced automatically through cryptography. No single actor can selectively change policies for any self-serving purpose.
Everything is applied uniformly and is censorship-resistant.
3. Publicly verifiable - The Newton Explorer ensures that every transaction and policy decision is openly available. It can be audited by anyone, which effectively gives the industry provable enforcement.
4. Native composability - One of the most important aspects of Newton is that the policies on the protocol can be reused across multiple apps, wallets, and chains.
This composability makes life easier for developers, users, and auditors, bringing holistic protection to the entire crypto ecosystem.
Beyond this, Newton Protocol is very complex from a technical standpoint. For the sake of this article, we’ll stick to what we consider the four most crucial components of its technical architecture, to give you a better understanding of why the protocol is so effective.
1. Policy definition - As mentioned earlier, policies are written in a high-level language such as Rego.
The reason behind this architectural choice is that it is flexible and modular. A policy for something as simple as a spending limit can be made, but policies for enforcing multiple conditions at once can also be made.
Another reason is that it’s updatable. Nothing in this world is ever stagnant. As rules and regulations evolve, so will the compliance requirements and risk controls. Therefore, policies can always be easily updated in accordance.
2. Validators - Newton Protocol has a decentralized network of AVSs that are responsible for evaluating transactions against the policies and generating proofs.
They play an essential role in ensuring that compliance remains valid, automated, and efficient.
Like any other blockchain network, these validators are economically bonded. They have some capital staked, which will be slashed if they act maliciously.
3. ZK proofs - All policies and risk controls aren’t the same. Some are more basic, while others involve the handling of sensitive information.
All policy evaluations on Newton Protocol have a cryptographic receipt attached, which can be given to third parties or regulators in case some sort of audit or evaluation is necessary.
But if the policy being evaluated contains sensitive information, a ZK proof will be used to verify compliance without revealing the information to any party.
It can’t be understated how crucial this is for the average user coming onchain.
4. Data providers - Newton Protocol utilizes oracles and other services that provide the data needed to enforce policy.
This could be things like price feeds, sanctions lists, geolocation checks, credentials, fraud detection signals, and so on.
They ensure that all necessary information is always available, preventing hiccups in the policy enforcement process.
With that, we have covered everything you need to know about Newton Protocol, crypto’s onchain policy engine.
But we still need to understand just how important it is and how big this thing could get.
The market opportunity
The market opportunity for Newton Protocol is virtually endless. It can span from DeFi to stablecoins to AI to traditional finance to real-world assets to basically anything in the vast $250 trillion asset market.
For the sake of this article, we’ll stick to just a couple of the big ones that may be a reality in the more immediate future to give you a sneak peek into what the industry could look like in a post-Newton Protocol world.
1. Institutional adoption
It’s no secret that institutional involvement in crypto has significantly ramped up as of January 2026. Whether it’s through ETFs, RWAs, tokenization, stablecoin issuance, or simple investment, the institutions are certainly here.
However, estimates suggest that institutions pumped in roughly $40 billion of capital. Although impressive, that’s barely a drop in the bucket when you compare it to the total assets under management for most of these financial institutions.
The reason for this cautious approach is that there are still a lot of grey areas in crypto.
Institutions are dealing with large sums of capital, and with that comes the responsibility to allocate it properly, protect clients, and most importantly, comply with the strict regulations that are imposed on them.
Doing this in crypto, especially in the open onchain world, is incredibly difficult.
A solution like Newton Protocol may just prove to be that solution needed to properly open the floodgates. Having complete customizability over risk controls effectively nullifies the compliance issue.
This then gives institutions the green light to not only pump in capital through investments but also to create their own financial applications, whether it be structured products, DeFi investment vehicles, stablecoins, or any other sort of financial instrument.

Magic Labs has already played its role in solving crypto’s adoption issues from the user side. They are now expanding their focus and playing their role in making it easy for institutions to get onboarded.
2. Stablecoin issuance
Stablecoins are easily one of the greatest innovations to come out of the crypto world.
They are unparalleled for payments, transfers, holding foreign currencies, and mass distribution. It’s simply a better version of fiat.
As the importance of stablecoins continues to grow even beyond crypto-native use cases, governments and institutions alike will have to stick their fingers in and grab a piece of the pie (if not the whole damn thing).
Newton simply allows stablecoin issuers to now have a verifiable policy layer attached to the stablecoin. So you get all the benefits of what makes stablecoins great while strengthening compliance controls natively onchain.
Based on the government's rulings, features such as sanctions screening, fraud detection, travel rules, and so on can be baked into the stablecoin's smart contract functionality. No need for expensive manual oversight.
3. RWAs and tokenization
The rising sector of real-world assets ($20 billion TVL) and tokenization could prove to be one of crypto’s biggest innovations, potentially surpassing stablecoins in the near future.
The ability to tokenize any asset with additional customizable functionality through smart contracts, making the entire system more efficient, is simply very powerful stuff.
The seeds for this sector are currently being sown, and there is no doubt that a couple of years down the line, we’ll see a lot of financial instruments operate onchain.
This is exactly why the market opportunity for Newton Protocol is virtually infinite.
In a world where every asset can be brought onchain, Newton Protocol will sit at the center of all these assets and financial products as the policy and compliance layer.
When bridging the traditional world to the onchain world, it cannot be done without strict risk controls and compliance being met. All Newton does is take away the technical heavy lift for RWA and tokenization applications with simple plug-in style compliance, which can be implemented in the smart contract.
Once that’s achieved, Newton Protocol will effectively power the entire asset market that’s onchain.
4. DeFi vaults
Even if we zoom in to a more granular use case, such as DeFi, Newton Protocol will play a major role in propelling the DeFi industry forward.
We’ve reached a stage in DeFi where we have a good amount of tried and tested innovations that are future-proof. Things like lending markets, AMMs, structured yield products, and so on. A lot of these protocols utilize vaults in their setups.
With Newton Protocol, a bunch of risk controls can be implemented into vault functionality to prevent them from being manipulated.
For example, there can be screening of users for geographical restrictions, risk scoring restrictions, sanctions screening, and affiliations with blacklisted/malicious addresses.
There can also be withdrawal caps, circuit breakers, velocity limits, and so on put in place to prevent draining events.
Even vault strategies can have guardrails to prevent interaction with new or high-risk protocols by using risk screening.
In actuality, by introducing compliance and risk controls to existing DeFi protocols, a likely scenario in the future is that, as more people manage their finances onchain, they will do so through DeFi protocols rather than applications built by TradFi players.
5. Minimizing exploit losses
In relation to the point above, Newton Protocol can also play a big role in minimizing losses from exploits.
There’s a saying in crypto that goes, “You’ve either been exploited, or you’re going to get exploited.” This is because with smart contracts, there is always a non-zero risk of getting hacked/exploited.
With this being a reality, Newton Protocol allows applications to implement certain risk controls.
Things like pre-transaction screening, banning addresses linked to malicious activity, sanctions screening, withdrawal caps, velocity limits, and circuit breakers, among other things, will prove very handy for onchain applications.
In the event of an exploit or anomalous behaviour, predefined onchain policies can provide automated response options, for example, pausing specific functions, tightening limits, requiring step-up verification, or routing activity through higher-assurance paths.
These mechanisms won’t prevent all losses, but they can reduce the blast radius and buy time to investigate and coordinate a remediation.
This shifts security from “improvise under pressure” to “precommitted controls,” allowing teams to focus more of their effort on building while keeping escalation paths clear when something goes wrong.
For users, the benefit is stronger, with more transparent guardrails around what the application can do under normal conditions and under stress.
This leads to more capital injection, which will fuel further innovation.
Concluding thoughts
Newton Protocol is actually bringing much-needed innovation to an industry that has otherwise been fairly starved of it over the last two years.
Building the first onchain shared risk protocol is not only an impressive feat but also a necessity.
The developer team already has a proven track record of solving adoption issues and gradually taking crypto closer and closer to mainstream adoption.
Magic Labs’ embedded wallet solution features 53 million+ wallets managed, over $10 billion+ in stablecoin volume processed, and over 200k developer signups.
Their focus has now expanded to take things to the next level. They’re looking to build infrastructure that makes crypto easy for institutions, governments, and mainstream audiences.
The world is coming onchain at some point in the future; that’s something most of us know. But there are still some hurdles that need to be crossed.
Newton Protocol is arguably crossing the biggest one, opening crypto to an unprecedented influx of capital and innovation.
If you’re looking at the bigger picture, then you should definitely be looking at Newton Protocol.
Thanks to the Newton Protocol team for unlocking this article. All of our research and references are based on public information available in documents, etc., and are presented by blocmates for constructive discussion and analysis. To read more about our editorial policy and disclosures at blocmates, head here.
























.webp)

.webp)
.webp)

%20(1).webp)


























































%202.webp)


.webp)

.webp)
.webp)
.webp)



.webp)





.webp)
.webp)

.webp)
.webp)
.webp)


.webp)
.webp)










.webp)


.webp)









.webp)







.webp)




.webp)

























.webp)







.webp)















.webp)

.webp)
.webp)

.webp)














.webp)
.webp)


.webp)







.webp)




